by Craig Cocciola | Nov 27, 2017 | Cyber Security, Cybersecurity Jobs
ABL Cyber Lab brings experience to Cyber Certification Courses
LAB Overview
The ABL Cyber Lab is for both beginner and intermediate level cyber skills building. The ABL Cyber Lab training programs provide students with an interactive environment to learn the use of powerful hacking tools to scan, attack, test and build the required real-world skills to discover website and application vulnerabilities. The Lab is a secure way to learn and practice on internal, non-public web servers. The Lab training is not conducted in controlled simulations. Users are provided lessons on ABL Lab servers which allow them to progressively learn in a safe environment. Through the use of tools in Kali Linux, they scan and discover flaws and weaknesses known to be used by attackers to compromise systems. By gaining the hands-on experience of offensive tactics, cyber security professionals are able to prepare and determine the most effective strategy for defense.
In addition to many others, Lab students learn Pen Testing and how to perform:
- Wireless Attacks
- using aircrack-ng, fern Wi-Fi and Kismet
- Web Application Analysis
- Burpsuite, OWASP-Zap, SQLmap, WPScan
- Sniffing and Spoofing
- Metasploit, ettercap, wireshark, netsniff-n
- Information Gathering
- netdiscover, NMap, recon-ng
- Cyber Exploitation Tools
- Social Engineering ToolKit, Metasploit, Armitage, BeEF
Cyber Lab Skills-Based Training
All ABL Cyber Lab students have access to over 200 Kali linux pre-installed tools. Upon completion of all Beginner and Intermediate Lab lessons, all students receive a Certificate of Completion. The Lab experience provides hands on experience which is critical to supplement industry standard certification preparation training. This combination ensures the individual has the knowledge and practical skills to add value to his/her team and help identify poorly designed code and vulnerable system configuration critical to protecting any organization.
Closing the gap in cybersecurity skills requires a national agenda to develop critical technical skills, cultivate a larger and more diverse workforce, and reform education and training programs to include more hands-on learning.
TOUR the ABL Cyber Lab: Take a 2 minute video tour of the ABL Cyber Lab, at the ABL Cyber Academy....
NOTE: ABL uses a fully vetted and tested video hosting services. These are Safe links.
- Wireless Attacks
- Web Application Analysis
- Sniffing and Spoofing
- Information Gathering
- Cyber Exploitation Tools
Many others…

Contact ABL Cyber Lab:
Craig Cocciola, FSO Director IT
480-525-7195 direct
craig@advancedbusinesslearning.com
by Craig Cocciola | Sep 7, 2017 | Cyber Security, Cybersecurity School, Ethical Hacker, News
Cybersecurity Jobs are Knocking – certifications will open the door
FACT: the number of job postings requiring IT or cybersecurity certifications, are far greater than the supply of those holding these credentials. College degree is NOT required to work and grow in IT or Cybersecurity careers.
visit: CyberSeek.org or DOWNLOAD 3192-CyberSeekFlyer-FINAL-online INFO SHEET
Available Cyber Career Analysis Tools
> Cybersecurity Supply And Demand Heat Map
> Cybersecurity Career Pathway
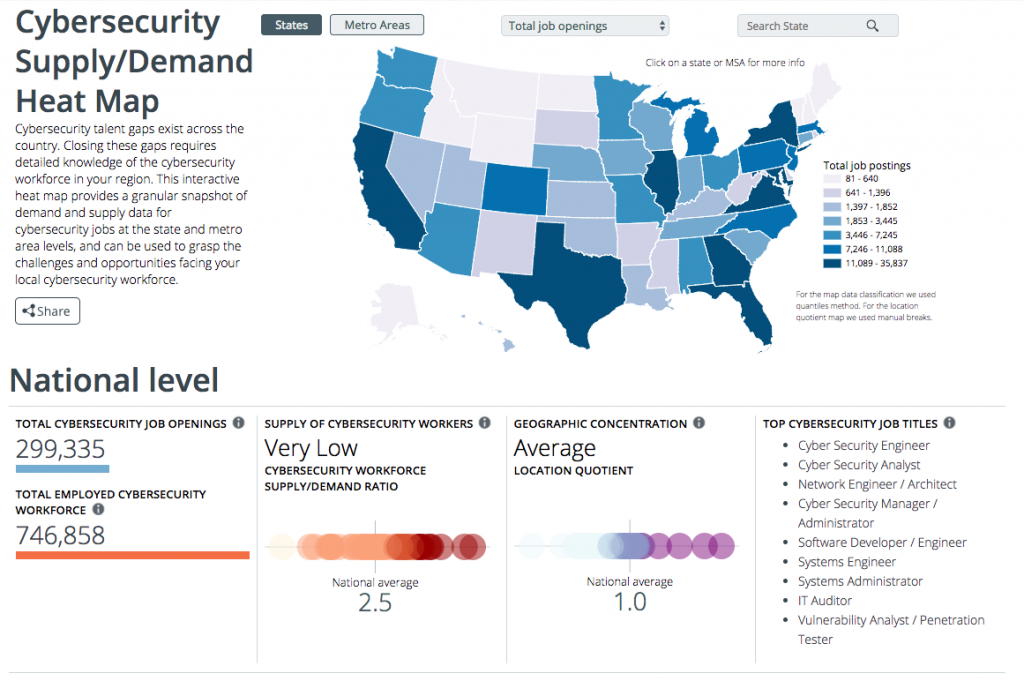
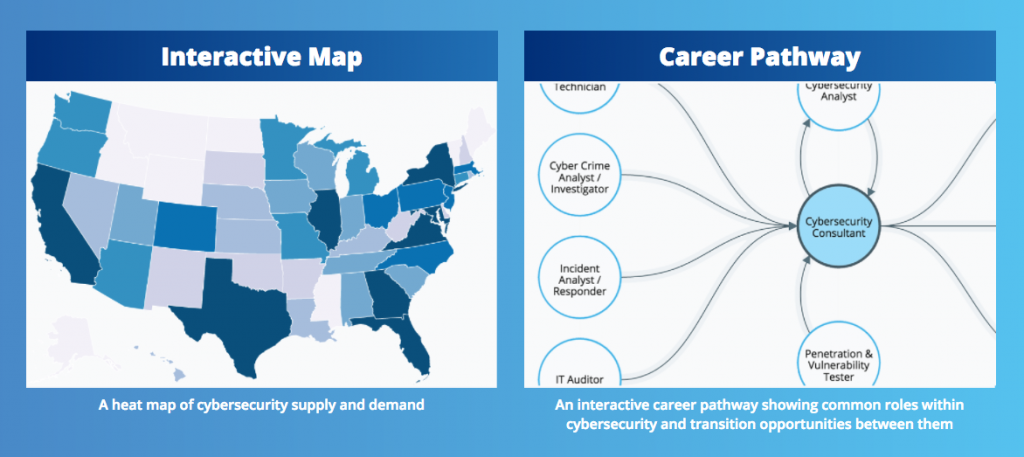
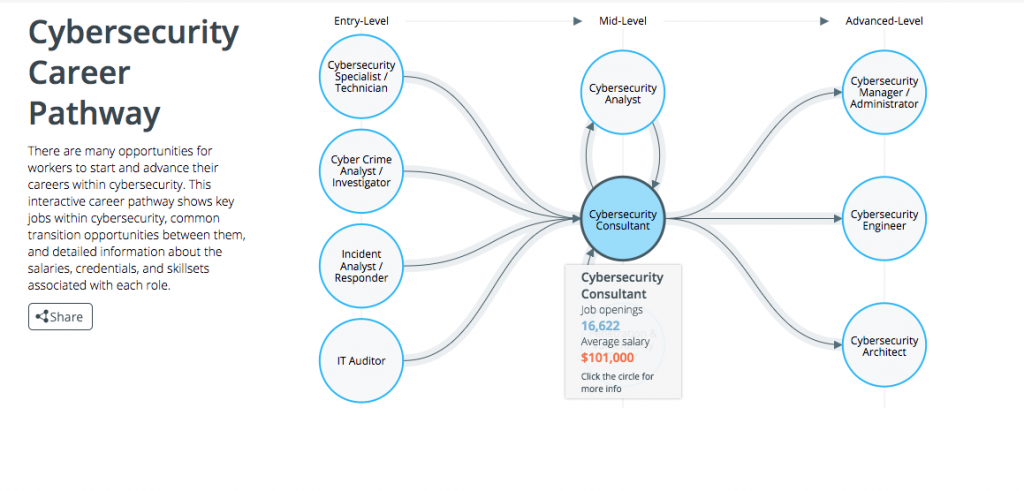
by Jason Jantzen | Sep 9, 2016 | CISSP Certification Arizona, CISSP PMP Security+, Cyber Security, Cybersecurity Certifications, Network+ Classes, News, PMP Certification AZ
Advanced Business Learning, (ABL) a Licensed State of Arizona postsecondary vocational school, now offering five-day cyber security boot-camp certification preparation courses with Federal Government pricing, at their classroom facility in Tempe.
Scottsdale, AZ (September 6, 2016) – Now offering Intelligence Community and Military Grade instruction, Scottsdale based Advanced Business Learning (ABL Academy) is currently enrolling for the following 5-day bootcamp cybersecurity training preparation courses:
CISSP: This certification preparation program is intended for experienced IT security-related practitioners, auditors, consultants, investigators, or instructors, including network or security analysts and engineers, network administrators, information security specialists, and risk management professionals, who are pursuing CISSP training and certification to acquire the credibility and mobility to advance within their current computer security careers or to migrate to a related career.
PMP: This certification preparation program is intended for individuals in various job roles who are involved in leading, managing, and participating in small to medium scale projects. In this course, students will apply recognized practices of project management and understand a project’s life cycle and roles and skills necessary to effectively initiate, plan, execute, monitor and control, and close a project.
Security +: This certification preparation program prepares technology professionals to master technology systems found in varied information technology environments, from traditional devices and operating systems to mobile platforms. This focus area provides the skills and knowledge to apply industry best practices along with new, innovative solutions to troubleshoot networking and security operations across a variety of information technology infrastructures and devices.
Network +: This certification preparation program for the CompTIA Network+ improves a technician’s competency in managing, maintaining, troubleshooting, installing, and configuring basic network infrastructure. This program validates the essential knowledge and skills needed to confidently design, configure, manage and troubleshoot any wired and wireless networks.
CEH: This certification preparation program is for individuals seeking the CEH certification. This program will significantly benefit security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure.
Class schedules will start in early October for CISSP; PMP; Security +; Network +; CEH and more. Visit www.advancedbusinesslearning.com/cyber-security for further details on classes or contact the ABL Academy at: 480-222-7507 or 480- 339- 4851.
About Advanced Business Learning (ABL)
For over 17 years, Advanced Business Learning has been a leader in workforce effectiveness programs serving the US Government and Fortune 1000 clients across the country and around the globe. Their team of elite consultants, instructors and best-of-breed partners are dedicated to delivering relevant, results-focused programs that are cost effective and have a measurable impact on your company’s short term goals and long term success.
Advanced Business Learning has a mission of bringing the same high quality DoD classroom experience with authorized CompTIA, EC-Counci, ISACA, ISC2, and PMI materials plus military grade instructors, many with DoD experience and Secret clearances, to thier certification exam prep courses where they ensure both certification exam readiness and application to real world work.
Media Contact:
Christine Holtz
Phoenix Marketing Associates
602-282-0202
by Jason Jantzen | Sep 6, 2016 | Cyber Security, Cybersecurity School, Ethical Hacker, News
Recent cyberattacks on corporations like Target, Banner Health and most recently public voter data have influenced corporations to take a much more offensive approach to their internal cybersecurity practices. As companies like Uber are shifting away from a traditional brick and mortar organization to a more cloud based platform, the need to protect consumer information has increased exponentially. Modern day ways of doing business now have much less to do with cash as they do a smart phone transaction.
To avoid any setbacks or loss of consumer trust, companies have been forced to rethink their approach to protecting consumer data from a “wait and see” to having skilled and educated employees in place who now take preemptive measures to test strategies and best practices before a breach occurs.
A recent study by CompTIA, a leading resource for the IT industry, has shown that companies now consider security one of the primary responsibilities of their IT team. Larger organizations may have a subset of individuals whose sole responsibility is protecting consumer data while other smaller companies rely on well trained individuals with Network+ or CISSP certifications leading the helm.
Long gone are the days where a simple firewall was sufficient security. Corporations must now assess vulnerability of data not only within but also vet the security capabilities of vendors with whom they work. An example of this would be third party credit card processors or cloud based CRM platforms like Salesforce who are trusted daily with detailed consumer information.
Regardless of the security measures a company takes, CompTIA has also found that the most common source of breached data is caused by human error—specifically untrained employees. Internal efforts to educate employees on cybersecurity best practices often fall short, creating a need for classroom based learning in a short amount of time.
Advanced Business Learning, a licensed State of Arizona postsecondary vocational school and a CompTIA Authorized Training Provider, offers a wide variety of courses which properly prepare workforces to meet today’s challenges in security management. Companies who wish to improve the knowledge base of their workforce can enroll employees in entry-level to advanced CompTIA courses which establish best practices in troubleshooting, networking and security across a variety of devices in a 5-day bootcamp. For those IT departments on the offensive, they may consider the investment in having their top IT professionals becoming ISC2 certified and ultimately becoming a Certified Information Systems Security Professional (CISSP).
by Craig Cocciola | Sep 1, 2016 | Cybersecurity Certifications, Cybersecurity School, Knowledge Center, News
Phoenix Cybersecurity Training School Offers New Learning Experience
As stout advocates against “learning decay” (the loss of retention of learned material over time) Advanced Business Learning (ABL) has developed a unique process that not only fights learning decay but helps students retain and relearn over time.
E-Learning (or web-based curriculum) done right involves working with the organization’s subject matter experts to distill the key skill-based learning elements and creating actionable scenarios the participant can immediately apply on their job. Couple this with targeted reinforcements to ensure just in time, just as needed rapid learning transference to the job.
To help stem this learning decay over a period of time and ensure the transfer of learning to actual job performance, a Continuous Learning System (CLS) should be incorporated into any learning solution. This is an inventory of tools and content designed to enhance learning sustainment by delivering reinforcement training in live, virtual, or blended environments.
This “menu” approach is intended to be “mixed and matched” and configured based on specific requirements, situations, and readiness levels. Examples of CLS elements include:
- Meetings in a box: Interactive discussions about best practices. Sustainability guides provide specific actions participants will take before, during, and after courses to promote the transfer and sustainability of learning
- E-toolkits/Mobile Learning: Electronic cache of performance application, reinforcement, and support tools for easy access to updated course materials. Posted content may include, but is not limited to, Best Practice analyses, lessons learned, job aids, media assets, sample communications, templates, social media sharing tools, blogs, technical manuals
One example of Mobile learning or M-learning is to create targeted learning at the fingertips of users. This can be accomplished via Quick Response Code (QR Codes) posted on key equipment that links to a Learning Management System providing immediate access to instruction manuals, videos, job aids, micro-learning elements and scenarios on how to use the equipment to help the individual be effective in working with that specific equipment.
Users with a camera phone/smart tablet/laptop equipped with the correct reader application can scan the image of the QR code to display text, contact information, connect to a wireless network, or open a web page in the browser. This act of linking from physical world objects is termed hard linking or object hyperlinking. QR codes can be used to log into websites: a QR Code is shown on the login page on a computer screen, and when a registered user scans it with a verified smartphone, they will automatically be logged in. Authentication is performed by the smartphone which contacts the internal server.
ABL’s unique approach to E-learning methods of training and processing information with continual technology-based reinforcement has proven to be a tactical advantage for employers looking to train their workforce. Employees are out-of-pocket for a short amount of time and return to work with a new base of expertise and the tools to retain the curriculum they just absorbed without a steep drop off from learning decay.




